By now, we’re all pretty used to doing a Google or Amazon search, then having ads pop up about the item you searched for.
Take that a step further: Have you walked into a business but didn’t buy anything? Then next time you check Facebook, an ad for that business appears on your feed?
Happened to me for the first time about a year ago. I went into an independent bookstore in Whitefish, Montana to make sure they still had copies of my book in stock. I left without purchasing anything.
When I got home, I happened to check Facebook. An ad popped up for that same bookstore. How did FB know I’d been there? I hadn’t Googled it. No credit card transaction had been processed to connect me to that store.
However, the smartphone in my pocket knew I’d been there.
The amount of data recorded by that device creeps me out…especially when I didn’t knowingly put the information into it.
Recently I made airline reservations on my laptop. When I opened the calendar on my smartphone to enter the flight times and numbers, they were already there. What the…? I purposely haven’t synced the laptop and smartphone to talk to each other.
Yes, it was convenient but it bothered me. What uncomfortable magic suddenly connected the two devices? It hadn’t occurred several months earlier when I last bought tickets from Delta, nor with American Airlines where I’d booked flights a week before. What had changed?
Somewhere hidden in terms and conditions, apparently a new provision allowed access to my phone. By whom? Google? Delta? The phone manufacturer?
If anyone more techie than I am (which means 99% of the population) can explain this, I’m all ears.
Stealth “permissions” sneak past us whenever we check that box: “I agree to the terms and conditions.” When you download a game, an app, or make a purchase, do you read all 47 pages of underlying legalese? Probably not. Additionally, since terms are often subject to unilateral change by the company without notice, what good does it do to read them?
We have traded privacy for convenience, one app at a time.
Smart devices invade our homes. Alexa eavesdrops 24/7 on conversations. In some instances, she has been known to broadcast private conversations to third parties, as happened to this Portland, OR family who learned their discussion about hardwood flooring had been shared with a person on their contact list.
So…in the privacy of your bedroom, what if you complain to your spouse about your rotten boss? Suppose the oh-so-helpful Alexa sees fit to send that conversation to that boss because s/he happens to be on your contact list. Ouch.
Never mind what else Alexa might overhear in your bedroom!
Lately my husband and I have been listening to a Michigan attorney named Steve Lehto on You Tube. He delivers short, entertaining podcasts about legal issues, specializing in vehicle warranties and lemon laws. Sometimes he goes off on an unrelated topic that catches his interest. This video addresses stealth permissions on smartphone apps.
Steve reveals that when you buy or lease an Android smartphone, it comes preloaded with certain apps including one that keeps track of keystrokes on the phone’s keyboard. Sounds innocuous, right?
Until you realize every text message, every bank PIN, and every credit card number you type is recorded. A record of those keystrokes may be available to whoever pays for that information.
Steve didn’t mention iPhones but it’s not a great leap to imagine they share similar apps.
Older devices like Blackberries have mechanical keyboards rather than electronic. You tap a key and a contact switch causes the letter to appear on the screen.
But smartphone keyboards are different. They record keystrokes electronically (known as “keylogging”) with no mechanical switch. Somewhere in cyberspace, someone is keeping track and storing every keystroke.
I don’t bank or pay bills online because hackers gallop miles ahead of safeguards. Security patches close the breach only after the horse is long gone out the barn door.
http://Embed from Getty Images
However, I do text. And that’s how the keystroke app slapped me in the face.
Last summer, an old friend visited us in Montana and left behind his small, well-worn Bible. A few weeks ago, he died in San Diego. At the time of his death we were away from our Montana home, on vacation in Florida, meaning we had to fly from Tampa to San Diego for the funeral.
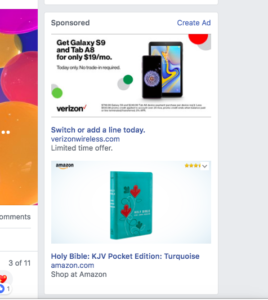
We wanted to take his Bible to the memorial so I texted our neighbor in Montana and asked him to look for it among the books stacked on our coffee table. I described it as a small, turquoise Bible. The neighbor found it and mailed it to us. All good.
Shortly afterward, an ad popped up on my Facebook feed…
…for a pocket Bible in turquoise.
Hmmm.
That unusual combination of keywords could only have come from the text I typed on my smartphone. Android recorded my private text message and passed it on to Facebook who passed it on to Amazon. Now I’m angry.
If you’re arrested on suspicion of a crime, the Fourth Amendment to the Constitution requires law enforcement to obtain a search warrant to dump the contents of your phone. The same rules obviously don’t apply to Facebook, Android, Apple, Google, Amazon, etc. because we give up those rights simply by using these convenient devices.
Keylogging apps are sold for legitimate purposes, like checking your minor children’s exploration of internet sites, or to see if they’re texting pals to sneak off to a forbidden kegger.
However, such apps are a hacker’s dream because passwords, bank PINs, credit card numbers, and other sensitive private information can become available to cybercriminals.
It’s like installing a deadbolt on your door then handing out keys to random people on the street.
Crime writers can imagine endless plots arising out of technology scenarios.
My thriller, Instrument of the Devil, was set in 2011 as smartphones first exploded in popularity. In the story, a terrorist hacks into the protagonist’s smartphone. He employs what was then secret technology to eavesdrop on her every word and track her physical location while he sets her up to take the fall for his crime—a cyberattack on the electric grid.
In 2019, those formerly covert apps are widely in use by anyone. They are everyday tools that allow tech giants to mine ever more intimate information about us.
As an author, I’m normally delighted when someone reads what I’ve written. However, as a human being, I resent this invasion into my personal communications.
A wise lawyer once told me, “Don’t put in writing anything you wouldn’t want to be read in open court.” I remember his advice now when I text because…
…Someone is always watching and listening.
Your turn, TKZers. Have you experienced creep-out moments due to technology? What nefarious plots can you imagine where smart devices play a role?
Instrument of the Devil is on sale for only 99 cents during January.